Category: Latest Internet News

Brevard County, located on the east coast of Florida, has been in the spotlight recently due to high-profile arrests and criminal incidents. The county, known for its beautiful beaches and vibrant community, has been shaken ...

Morning exercise is great for starting your day on the right foot. It sets a positive tone for the rest of the day and can significantly impact your physical and mental well-being. Whether it’s ...

National media has reported that China’s former net censor, who once held excessive-profile conferences with industry leaders, including Apple chief executive Tim Cook and Facebook founder Mark Zuckerberg, is a status trial on corruption allegations. ...

There is a capacity for Samoans to “paintings remotely” with the use of distant places technology companies due to the upgrading of Samoa’s submarine cable gadget so that you can offer low-cost, excessive-velocity net. Minister ...

What could we do without mothers, am I right? Even once they embarrass us, you’ve nonetheless gotta love ’em. Well, permit’s say that Pieter Hanson — after seeing what his Mom published on Twitter this ...

Tech innovation center Digital Catapult has released the UK’s modern-day 5G testbed in Brighton & Hove, with the Coast to Capital nearby organization partnership, digital networking discussion board Wired Sussex, and the University of Brighton. ...
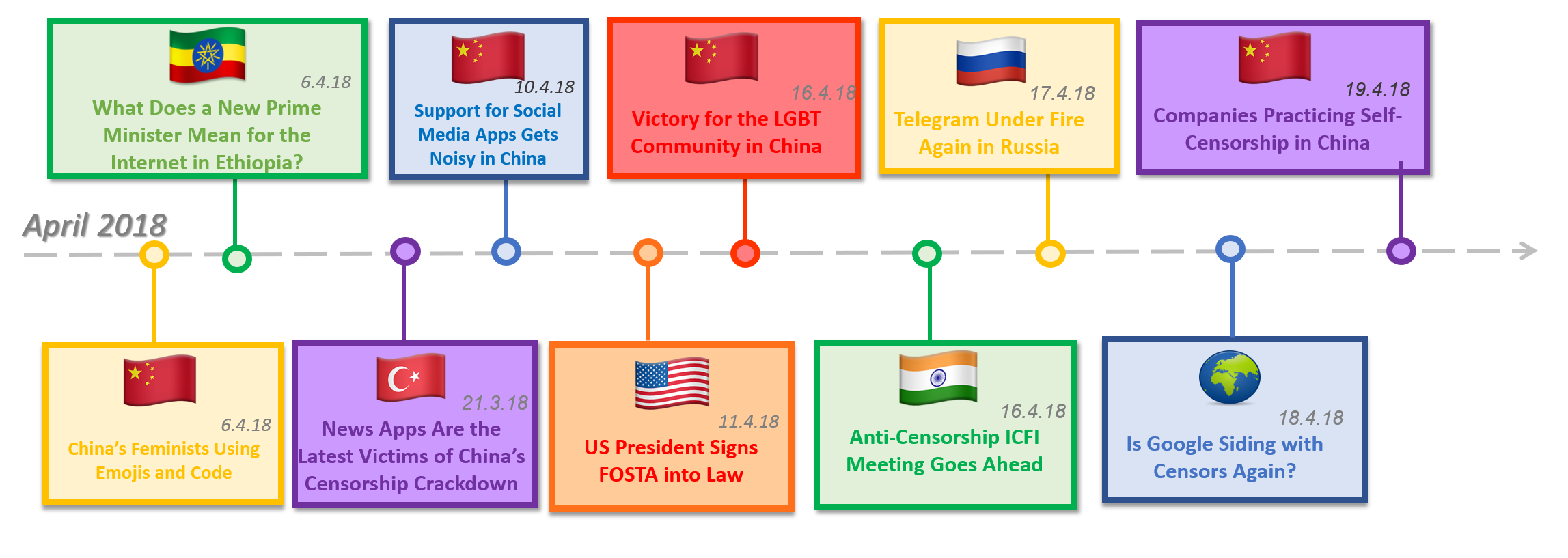
China has closed down more than 4,000 websites and online debts in a 3-month campaign against ‘dangerous’ online data, the United States state media suggested. China continues to put the internet under tight manipulation and ...

Hang on, I thought Tom Hiddleston become the net’s boyfriend. No, the internet ghosted him when he appeared bizarre around Taylor Swift. Take into account? Right, however, what about Jeff Goldblum? Jeff Goldblum becomes by ...

Industrial Internet Services (IIoT) has the vital intention to enhance operational productiveness and computerize paperwork in firms. Besides, businesses embrace progress by breaking down units to realize improvement openings in unique areas. Organizations might send ...

Though the wave of Kiki challenge is now all settled down, and the social media would ultimately make feel? Oh, how may I want to you? Social media never fails to amaze us. With challenges ...